Product:
Cognos Analytics 11.0.12
Microsoft Windows 2016 server
Problem:
After apply stronger TLS security demand with the tool IIS Crypto, to apply to VISA and MASTERCARD data regulation ( PCI DSS ), on a IIS server for Cognos, users of Firefox or Chrome can not surf to it with HTTPS. IE is still working fine.
Error message:
NS_ERROR_NET_INADEQUATE_SECURITY or ERR_SPDY_INADEQUATE_TRANSPORT_SECURITY
Background:
https://www.nartac.com/Products/IISCrypto
The IIS Crypto 2 tool is run on the server to apply the settings, using a template file. Here is a example how you can do it https://gist.github.com/JimWolff/fc35d863db8971b2a73c96f90c5002e4
Part of the template file is this cipher settings listed as below:
<cipherSuites>
<cipherSuiteItem name=”TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P521″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P384″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384_P256″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P521″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P384″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256_P256″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P521″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P384″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA_P256″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P521″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P384″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA_P256″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384_P521″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384_P384″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P521″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P384″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256_P256″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384_P521″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384_P384″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P521″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P384″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256_P256″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P521″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P384″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA_P256″ state=”Enabled” />
<cipherSuiteItem name=”TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA_P521″ state=”Enabled” />
<cipherSuiteItem name=”TLS_RSA_WITH_AES_256_GCM_SHA384″ state=”Disabled” />
<cipherSuiteItem name=”TLS_RSA_WITH_AES_128_GCM_SHA256″ state=”Disabled” />
<cipherSuiteItem name=”TLS_RSA_WITH_AES_256_CBC_SHA256″ state=”Disabled” />
<cipherSuiteItem name=”TLS_RSA_WITH_AES_128_CBC_SHA256″ state=”Disabled” />
<cipherSuiteItem name=”TLS_RSA_WITH_AES_256_CBC_SHA” state=”Disabled” />
<cipherSuiteItem name=”TLS_RSA_WITH_AES_128_CBC_SHA” state=”Disabled” />
<cipherSuiteItem name=”TLS_RSA_WITH_3DES_EDE_CBC_SHA” state=”Disabled” />
<cipherSuiteItem name=”TLS_DHE_RSA_WITH_AES_256_GCM_SHA384″ state=”Disabled” />
<cipherSuiteItem name=”TLS_DHE_RSA_WITH_AES_128_GCM_SHA256″ state=”Disabled” />
<cipherSuiteItem name=”TLS_DHE_DSS_WITH_AES_256_CBC_SHA256″ state=”Disabled” />
<cipherSuiteItem name=”TLS_DHE_DSS_WITH_AES_128_CBC_SHA256″ state=”Disabled” />
<cipherSuiteItem name=”TLS_DHE_DSS_WITH_AES_256_CBC_SHA” state=”Disabled” />
<cipherSuiteItem name=”TLS_DHE_DSS_WITH_AES_128_CBC_SHA” state=”Disabled” />
<cipherSuiteItem name=”TLS_DHE_DSS_WITH_3DES_EDE_CBC_SHA” state=”Disabled” />
<cipherSuiteItem name=”TLS_RSA_WITH_RC4_128_SHA” state=”Disabled” />
<cipherSuiteItem name=”TLS_RSA_WITH_RC4_128_MD5″ state=”Disabled” />
<cipherSuiteItem name=”TLS_RSA_WITH_NULL_SHA256″ state=”Disabled” />
<cipherSuiteItem name=”TLS_RSA_WITH_NULL_SHA” state=”Disabled” />
<cipherSuiteItem name=”SSL_CK_RC4_128_WITH_MD5″ state=”Disabled” />
<cipherSuiteItem name=”SSL_CK_DES_192_EDE3_CBC_WITH_MD5″ state=”Disabled” />
</cipherSuites>
Templates can be found here https://gist.github.com/JimWolff
Suggested Solution:
Add two cipher suites to the template file, and reboot the server to apply the new settings.
<cipherSuiteItem name=”TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384″ state=”Enabled” minimumOSVersion=”Windows2016″ />
<cipherSuiteItem name=”TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256″ state=”Enabled” minimumOSVersion=”Windows2016″ />
Should make the file to look like this
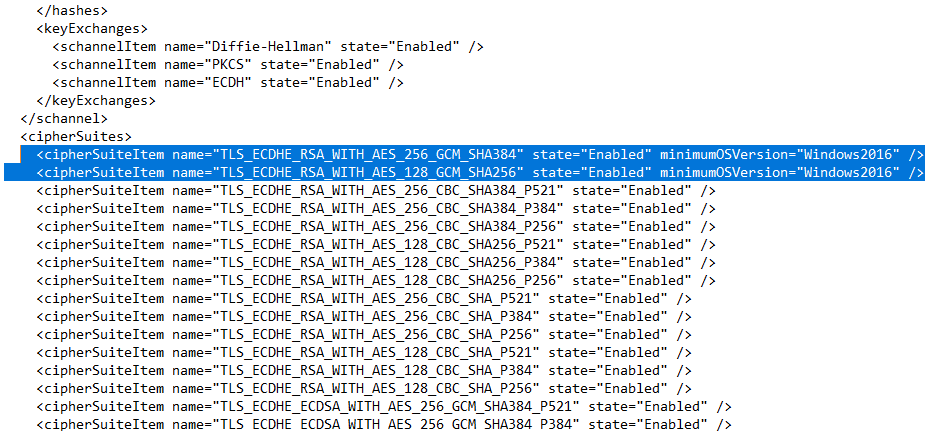
After this change, and you have applied it with the IIS Crypto 2 program, test if it works in Firefox or Chrome.
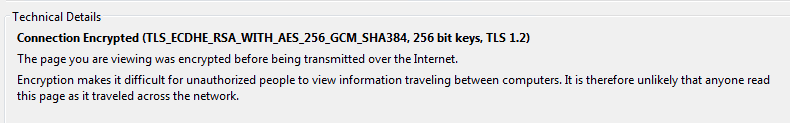
If you inspect the certificate in Firefox – you can see above information about the SSL in use.
Some of The changes are stored in the registry key [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL]
More information:
https://social.technet.microsoft.com/Forums/windowsserver/en-US/5e17d836-39f7-4246-a382-b073d1130079/ssl-cipher-suite-order-best-practice?forum=winserversecurity
https://docs.microsoft.com/en-us/windows-server/security/tls/tls-schannel-ssp-changes-in-windows-10-and-windows-server
https://docs.microsoft.com/en-us/windows-server/security/tls/tls-registry-settings#ciphersuites
https://docs.microsoft.com/en-us/powershell/module/tls/?view=win10-ps
https://tls.mbed.org/supported-ssl-ciphersuites
A Cipher Best Practice: Configure IIS for SSL/TLS Protocol
https://support.microsoft.com/en-ph/help/3140245/update-to-enable-tls-1-1-and-tls-1-2-as-default-secure-protocols-in-wi
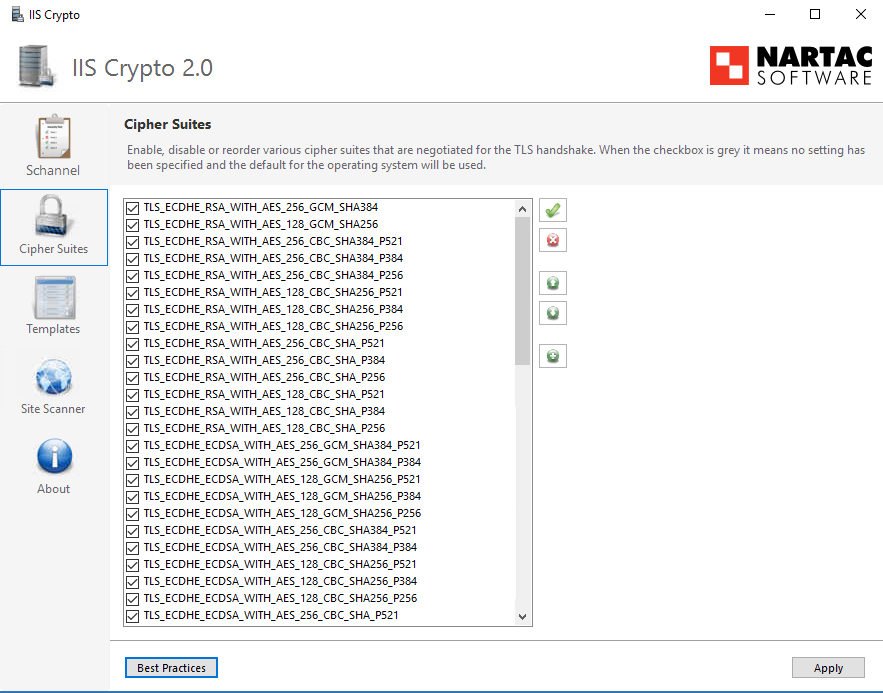
The Best Practices setup by the IIS Crypto 2 tool is:
<?xml version=”1.0″ encoding=”utf-16″?>
<iisCryptoTemplate xmlns:xsi=”http://www.w3.org/2001/XMLSchema-instance” xmlns:xsd=”http://www.w3.org/2001/XMLSchema” version=”0″>
<header>
<name>Best Practices</name>
<author>Nartac Software</author>
<lastUpdated>2019-01-21T13:47:28.1977801Z</lastUpdated>
<description>This template sets your server to use the best practices for TLS. It aims to be compatible with as many browsers as possible while disabling weak protocols and cipher suites.</description>
<builtIn>false</builtIn>
</header>
<schannel setClientProtocols=”true”>
<clientProtocols>
<schannelItem name=”Multi-Protocol Unified Hello” state=”Disabled” />
<schannelItem name=”PCT 1.0″ state=”Disabled” />
<schannelItem name=”SSL 2.0″ state=”Disabled” />
<schannelItem name=”SSL 3.0″ state=”Disabled” />
<schannelItem name=”TLS 1.0″ state=”Enabled” />
<schannelItem name=”TLS 1.1″ state=”Enabled” minimumOSVersion=”Windows2008R2″ />
<schannelItem name=”TLS 1.2″ state=”Enabled” minimumOSVersion=”Windows2008R2″ />
</clientProtocols>
<serverProtocols>
<schannelItem name=”Multi-Protocol Unified Hello” state=”Disabled” />
<schannelItem name=”PCT 1.0″ state=”Disabled” />
<schannelItem name=”SSL 2.0″ state=”Disabled” />
<schannelItem name=”SSL 3.0″ state=”Disabled” />
<schannelItem name=”TLS 1.0″ state=”Enabled” />
<schannelItem name=”TLS 1.1″ state=”Enabled” minimumOSVersion=”Windows2008R2″ />
<schannelItem name=”TLS 1.2″ state=”Enabled” minimumOSVersion=”Windows2008R2″ />
</serverProtocols>
<ciphers>
<schannelItem name=”NULL” state=”Disabled” />
<schannelItem name=”DES 56/56″ state=”Disabled” />
<schannelItem name=”RC2 40/128″ state=”Disabled” />
<schannelItem name=”RC2 56/128″ state=”Disabled” />
<schannelItem name=”RC2 128/128″ state=”Disabled” />
<schannelItem name=”RC4 40/128″ state=”Disabled” />
<schannelItem name=”RC4 56/128″ state=”Disabled” />
<schannelItem name=”RC4 64/128″ state=”Disabled” />
<schannelItem name=”RC4 128/128″ state=”Disabled” />
<schannelItem name=”Triple DES 168″ state=”Enabled” />
<schannelItem name=”AES 128/128″ state=”Enabled” />
<schannelItem name=”AES 256/256″ state=”Enabled” />
</ciphers>
<hashes>
<schannelItem name=”MD5″ state=”Enabled” />
<schannelItem name=”SHA” state=”Enabled” />
<schannelItem name=”SHA 256″ state=”Enabled” minimumOSVersion=”Windows2008R2″ />
<schannelItem name=”SHA 384″ state=”Enabled” minimumOSVersion=”Windows2008R2″ />
<schannelItem name=”SHA 512″ state=”Enabled” minimumOSVersion=”Windows2008R2″ />
</hashes>
<keyExchanges>
<schannelItem name=”Diffie-Hellman” state=”Enabled” />
<schannelItem name=”PKCS” state=”Enabled” />
<schannelItem name=”ECDH” state=”Enabled” />
</keyExchanges>
</schannel>
<cipherSuites>
<cipherSuiteItem name=”TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384″ state=”Enabled” minimumOSVersion=”Windows2016″ />
<cipherSuiteItem name=”TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256″ state=”Enabled” minimumOSVersion=”Windows2016″ />
<cipherSuiteItem name=”TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384″ state=”Enabled” minimumOSVersion=”Windows2016″ />
<cipherSuiteItem name=”TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256″ state=”Enabled” minimumOSVersion=”Windows2016″ />
<cipherSuiteItem name=”TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA” state=”Enabled” minimumOSVersion=”Windows2016″ />
<cipherSuiteItem name=”TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA” state=”Enabled” minimumOSVersion=”Windows2016″ />
<cipherSuiteItem name=”TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384″ state=”Enabled” minimumOSVersion=”Windows2016″ />
<cipherSuiteItem name=”TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256″ state=”Enabled” minimumOSVersion=”Windows2016″ />
<cipherSuiteItem name=”TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384″ state=”Enabled” minimumOSVersion=”Windows2016″ />
<cipherSuiteItem name=”TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256″ state=”Enabled” minimumOSVersion=”Windows2016″ />
<cipherSuiteItem name=”TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA” state=”Enabled” minimumOSVersion=”Windows2016″ />
<cipherSuiteItem name=”TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA” state=”Enabled” minimumOSVersion=”Windows2016″ />
<cipherSuiteItem name=”TLS_RSA_WITH_AES_256_GCM_SHA384″ state=”Enabled” />
<cipherSuiteItem name=”TLS_RSA_WITH_AES_128_GCM_SHA256″ state=”Enabled” />
<cipherSuiteItem name=”TLS_RSA_WITH_AES_256_CBC_SHA256″ state=”Enabled” />
<cipherSuiteItem name=”TLS_RSA_WITH_AES_128_CBC_SHA256″ state=”Enabled” />
<cipherSuiteItem name=”TLS_RSA_WITH_AES_256_CBC_SHA” state=”Enabled” />
<cipherSuiteItem name=”TLS_RSA_WITH_AES_128_CBC_SHA” state=”Enabled” />
<cipherSuiteItem name=”TLS_RSA_WITH_3DES_EDE_CBC_SHA” state=”Enabled” />
<cipherSuiteItem name=”TLS_DHE_RSA_WITH_AES_256_GCM_SHA384″ state=”Disabled” />
<cipherSuiteItem name=”TLS_DHE_RSA_WITH_AES_128_GCM_SHA256″ state=”Disabled” />
<cipherSuiteItem name=”TLS_DHE_DSS_WITH_AES_256_CBC_SHA256″ state=”Disabled” />
<cipherSuiteItem name=”TLS_DHE_DSS_WITH_AES_128_CBC_SHA256″ state=”Disabled” />
<cipherSuiteItem name=”TLS_DHE_DSS_WITH_AES_256_CBC_SHA” state=”Disabled” />
<cipherSuiteItem name=”TLS_DHE_DSS_WITH_AES_128_CBC_SHA” state=”Disabled” />
<cipherSuiteItem name=”TLS_DHE_DSS_WITH_3DES_EDE_CBC_SHA” state=”Disabled” />
<cipherSuiteItem name=”TLS_RSA_WITH_RC4_128_SHA” state=”Disabled” />
<cipherSuiteItem name=”TLS_RSA_WITH_RC4_128_MD5″ state=”Disabled” />
<cipherSuiteItem name=”TLS_RSA_WITH_NULL_SHA256″ state=”Disabled” />
<cipherSuiteItem name=”TLS_RSA_WITH_NULL_SHA” state=”Disabled” />
<cipherSuiteItem name=”SSL_CK_RC4_128_WITH_MD5″ state=”Disabled” />
<cipherSuiteItem name=”SSL_CK_DES_192_EDE3_CBC_WITH_MD5″ state=”Disabled” />
<cipherSuiteItem name=”TLS_DHE_RSA_WITH_AES_256_CBC_SHA” state=”Disabled” />
<cipherSuiteItem name=”TLS_DHE_RSA_WITH_AES_128_CBC_SHA” state=”Disabled” />
<cipherSuiteItem name=”TLS_PSK_WITH_AES_256_GCM_SHA384″ state=”Disabled” />
<cipherSuiteItem name=”TLS_PSK_WITH_AES_128_GCM_SHA256″ state=”Disabled” />
<cipherSuiteItem name=”TLS_PSK_WITH_AES_256_CBC_SHA384″ state=”Disabled” />
<cipherSuiteItem name=”TLS_PSK_WITH_AES_128_CBC_SHA256″ state=”Disabled” />
<cipherSuiteItem name=”TLS_PSK_WITH_NULL_SHA384″ state=”Disabled” />
<cipherSuiteItem name=”TLS_PSK_WITH_NULL_SHA256″ state=”Disabled” />
</cipherSuites>
</iisCryptoTemplate>
Workaround in firefox
Open Firefox and type about:config in the address bar
Click on I Accept The Risk
Search for network.http.spdy.enabled.http2
Change the value to False
Restart your browser