Product:
Cognos Analytics 11.1.7
Microsoft Windows 2016 server
Microsoft SQL server
Issue:
New installation of CA11. At start the IBM cognos service take long time to start. But the JAVA.EXE spins up to 6 GB ram and then crash and start over.
Errors like this are found log cbs_run_WebSphereLiberty.log:
Fri Aug 27 11:28:08 2021 INFO t[e20] CBSBootstrapService attempt to load config from “D:\Program Files\ibm\cognos\analytics\.\bin64\./bootstrap_wlp_winx64.xml”
Fri Aug 27 11:28:11 2021 ERROR t[e20] CBSSocketCommand failed to connect, CAM error: <errorDetail><errorCode>-12</errorCode><errorMessage>CAM-CRP-0026 The underlying socket: ‘10.123.123.65:9300’ returned an error.</errorMessage><errorStack><errorCode>10061</errorCode><errorMessage>Could not connect the socket, errno: 0x274d(10061)</errorMessage>
Error found in windows event log:
Faulting application name: cogbootstrapservice.exe, version: 11.1.5.2, time stamp: 0x5daf2515
Faulting module name: ntdll.dll, version: 10.0.14393.4530, time stamp: 0x60e33cac
Exception code: 0xc0000374
Fault offset: 0x00000000000f7153
Faulting process id: 0x960
Faulting application start time: 0x01d79b1621caeb73
Faulting application path: D:\Program Files\ibm\cognos\analytics\bin64\cogbootstrapservice.exe
Faulting module path: C:\Windows\SYSTEM32\ntdll.dll
Thu Aug 26 20:59:12 2021 WARN t[1908] CBSSockSendAction did not detect success string in response.
Thu Aug 26 21:00:14 2021 ERROR t[1908] PingChildProcess ping loop: process “wlp” is not active, so restarting it.
Thu Aug 26 21:00:52 2021 ERROR t[1908] CBSSocketCommand failed to connect, CAM error: <errorDetail><errorCode>-12</errorCode><errorMessage>CAM-CRP-0026 The underlying socket: ‘172.10.10.123:9300’ returned an error.</errorMessage><errorStack><errorCode>10061</errorCode><errorMessage>Could not connect the socket, errno: 0x274d(10061)
Error in Cognos Configuration at start:
[ ERROR ] CFG-ERR-0106 IBM Cognos Configuration did not receive a response from the IBM Cognos service in the time allotted.
Check that IBM Cognos service is available and properly configured.
16:31:03, ‘LogService’, ‘StartService’, ‘Success’.
Suggested solution:
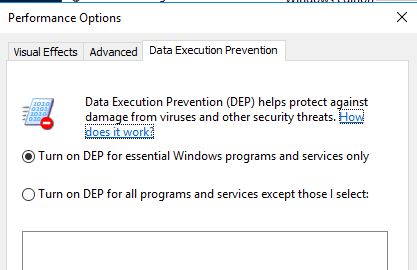
Ensure DEP is only for needed processes.
Check that the if the server have two network cards, they are correct configured.
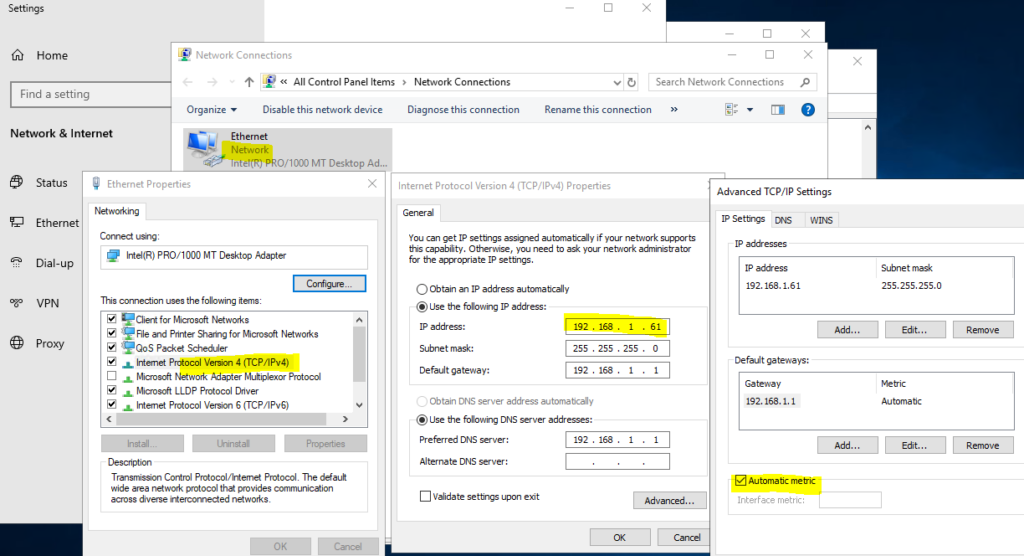
Check that the IP address and interface metric is not the same as other cards on the server.
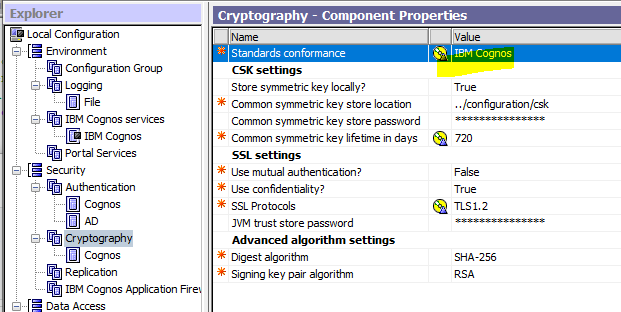
Test to change to IBM cognos instead of NIST SP 800-131A.
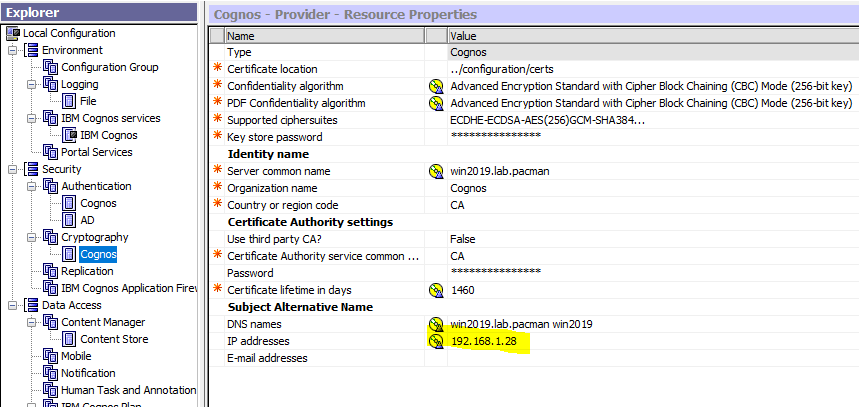
Check that the IP addresses in cognos configuration is then one of your server.
Check for ports in use with DOS command: netstat -a | find “9300”
Export the configuration, and recreate the crypto keys; like this
1. Stop the running of your service in Cognos Configuration.
2. On the Content Manager computer, click ‘File > Export As’.
3. Choose ‘Yes’ at the prompt and save the file. For example, name it ‘backup.xml’ which will be stored in the c11\configuration folder.
4. Close Cognos Configuration.
5. On the Content Manager computer
5.1 Create a backup of the following files before moving them to a different, secure location (as during the cryptographic keys regeneration process they will be re-created):
The files are:
· c11/configuration/cogstartup.xml
· c11/configuration/caSerial
· c11/configuration/certs/CAMCrypto.status
· c11/configuration/certs/CAMKeystore
· c11/configuration/certs/CAMKeystore.lock
· c11/temp/cam/freshness
5.2 Create a backup of the following directories before moving it to a different, secure location (as during the cryptographic keys regeneration process they will be re-created). Alternatively you can also rename the directories.
The directory is
· c11/configuration/csk
6. In the c11\configuration folder, rename ‘backup.xml’ to ‘cogstartup.xml’.
7. Open Cognos Configuration, save the configuration and start the services.
Restart windows server and see if that helps.
More information:
https://www.ibm.com/support/pages/node/286475
https://www.ibm.com/docs/en/cognos-analytics/11.1.0?topic=problems-starting-cognos-analytics
https://www.ibm.com/support/pages/faulting-application-name-cogbootstrapserviceexe-0xc0000374-error-event-viewer-when-starting-ibm-cognos-service
https://www.ibm.com/support/pages/error-starting-cognos-service-cogbootstrapserviceexe-application-error
https://www.ibm.com/support/pages/node/6379144
https://www.cognoise.com/index.php?topic=14377.0
https://www.ibm.com/support/pages/cognos-service-will-not-start-process-wlp-not-active
https://www.ibm.com/support/pages/dpr-err-2109-dispatcher-cannot-service-request-time-dispatcher-still-initializing-cognos-analytics
https://www.ibm.com/support/pages/node/6386326
https://www.ibm.com/support/pages/cognos-analytics-11-flipper-diagnostic