Product:
Cognos Analytics 11.1.4
Microsoft Windows 2019 server
Issue:
How request and use external certificate for CA11 internal communication, e.g. port 9300?
If both internal and external connections use HTTPS, then you can use port 9300 for HTTPS. Otherwise you need to set a separate port number for the HTTPS services, suggestion 9334 or 9443.
Solution:
The IKEYMAN tool allows you to include more fields for your certificate request. This instruction is hard to find, so a copy is provided here.
You need to do the steps on all your CA11 servers, but you start with the Content Manager server first.
1. Ensure that all IBM Cognos component services in the environment are shut down. Close any IBM Cognos Configuration that is open.
2. Copy the complete <cognos>\configuration directory to a safe place and name it configuration_original. At any point, this backup configuration directory can be restored to bring the state of the cryptographic keys for this component back to the original state.
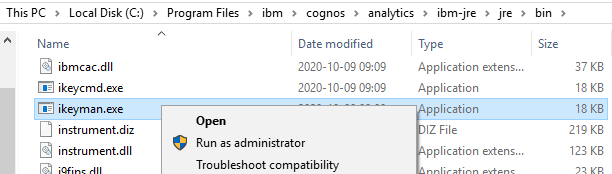
3. Run iKeyman.exe as administrator (or ./ikeyman for linux/unix users) from C:\Program Files\ibm\cognos\analytics\ibm-jre\jre\bin (for IBM Cognos 11.1.X+). For IBM Cognos 11.0.13 and lower versions, the path is <cognos>\jre\bin.
4. Click the folder with the curved arrow icon at the top of the window. In the open dialog panel, select PCKS12 as the Key Database Type, then browse to the <cognos>\configuration\certs directory and select CAMKeystore. Click OK. The default password is NoPassWordSet.
Generating a Certificate Signing Request (CSR):
5. Once the CAMKeystore loads, there are two certificates under the Personal Certificates drop down: ca and encryption.
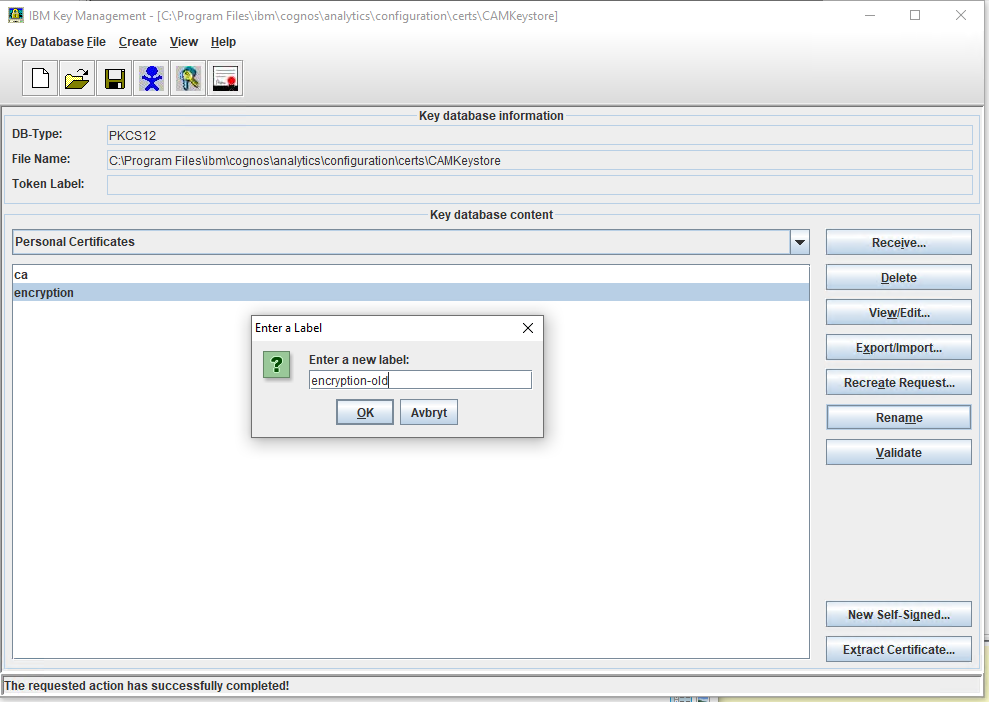
6. Select the encryption certificate and rename it to encryption_old.
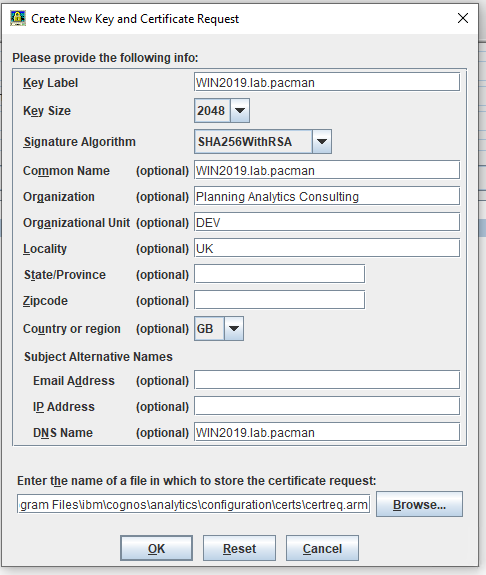
7. Select Create at the top of the iKeyman window, then click New Certificate Request. Make sure that Key Label is called “encryption“. The recommended Key Size is 2048 and the recommended Signature Algorithm is SHA256WithRSA.
The rest of the details can be completed as necessary. Multiple DNS names separated by a comma or a space can be used as well.
8. The CSR is called certreq.arm and it is located in <cognos>\configuration\certs. Give the certreq.arm to the certificate authority to generate the signed certificates.
9. Take another backup of the <cognos>\configuration directory and store it in a safe place. Name it “configuration_with_CSR“.
10. If the certificate authority returns two or three separate certificate files (root, intermediate (optional), and server certificates), in iKeyman, ensure that the Personal Certificates dropdown is set, then select Receive. Select only the server certificate.
If there is a dialog box that mentions that the CA (root certificate) is missing, click OK, and the encryption certificate is highlighted in yellow or the encryption certificate will be listed alongside the ca and encryption_old certificate.
Change the Personal Certificates drop down to Signer Certificates, then select Add and import the root certificate and intermediate certificate if the certificate authority returned one. The labels can be named root and intermediate.
If the certificate authority returns one file containing the certificates (.pem or .p12), click Receive or Add in either the Personal or Signer Certificates drop down, and select “Import all” at the prompt. All of the certificates are placed in their correct section.
11. Open Cognos Configuration. Under Environment, change these URIs to https:
- Gateway URI
- Dispatcher URIs for gateway
- Controller URI for gateway
- External and Internal dispatcher URI
- Dispatcher URI for external applications
- Content Manager URI
12. Under Cryptography > Cognos, switch “Use third-party CA?” to True.
Also, change the following to match the values used for the CSR in step 7:
- Server common name (CN)
- Organization name (O)
- Country or region code (C)
Change the DNS Names field under Subject Alternative Name to match the DNS name(s) that were used during the generation of the CSR in Step 7.
13. Save the configuration and start the IBM Cognos services.
Important Note: During this process, IBM Cognos Configuration cannot be opened and the IBM Cognos Services cannot be started until these steps are completed. If the certificate authority takes some time to send the signed certificates, consider using the Third-Party Certificate Tool method instead.
More information:
The DOS program supports 3 values in the request;
ThirdPartyCertificateTool.(bat|sh) -c -e
[-p keystore_password] -a key_pair_algorithm
-r path_to_cert_or_csr
-d dn
[-H subject_alternative_nameDns_name_dn]
[-I subject_alternative_ip_addresses]
[-M subject_alternative_email_addresses]