Product:
Cognos Controller 10.4.2 IF4 (CONTRL_UPDATE_version=CCR-AW64-ML-RTM-10.4.2000.1020-0)
Cognos Analytics 11.0.13
Microsoft Windows 2012 R2 server
Problem:
How setup Controller web in the new version?
When the Windows IIS server for CA11 is using HTTPS.
Solution:
Follow the official instructions here https://www.ibm.com/support/pages/how-install-controller-web
https://www.ibm.com/support/pages/how-configure-controller-web-use-cognos-cam-authentication
https://www.ibm.com/support/pages/how-configure-controller-web-use-ssl-https
This are the steps;
Ensure that you during setup can browse to cognos analytics iis server on both http and https.
Controller web frontend and backend are installed on the same Windows server.
Open server.env file from folder C:\Program Files\IBM\cognos\ccr_64\fcmweb\wlp\etc\
Change to: JAVA_HOME=C:/Program Files/IBM/cognos/ccr_64/fcmweb/jre
Open jvm.options file from folder C:\Program Files\IBM\cognos\ccr_64\fcmweb\wlp\etc\
Change last in file to:
-Xms4g
-Xmx8g
(depending on number of users and memory on the Windows Server)
Save the files.
Start a CMD command prompt as Administrator
Go to folder C:\Program Files\IBM\cognos\ccr_64\fcmweb
Enter command: SyncDBConf.bat ..\Data wlp\usr\shared\config\datasources
In file explorer go to C:\Program Files\IBM\cognos\ccr_64\fcmweb\wlp\usr\servers\fcm.web
Open com.ibm.cognos.fcm.web.properties file in notepad++
Change to: ccrwsUrl=http://cognosserver.company.com/ibmcognos/controllerserver/ccrws.asmx
and update also;
biUrl=http://cognosserver.company.com/ibmcognos/bi/v1/disp
biDispatchEndpoint=http://cognosserver.company.com:9300/p2pd/servlet/dispatch
loginMode=CAM
logoutMode.logoutCam=true
# pdfFont=C:/windows/fonts/Arial.ttf
Save the files with this changes.
Map up the c drive of the cognos analytics server and go to folder C:\Program Files\IBM\cognos\analytics\templates\ps\portal\ and create the text file variables_CCRWeb.xml
In notepad++ enter this values:
<CRNenv c_cmd=”http://controllerwebserver.company.com:443/#!/CamLogin”>
<cookies>
<param name=”cam_passport”/>
</cookies>
</CRNenv>
Save it inside file variables_CCRWeb.xml.
Restart the IBM Cognos Controller Web Windows service.
Go to folder C:\Program Files\IBM\cognos\ccr_64\frontend
Open config.js file in Notepad++
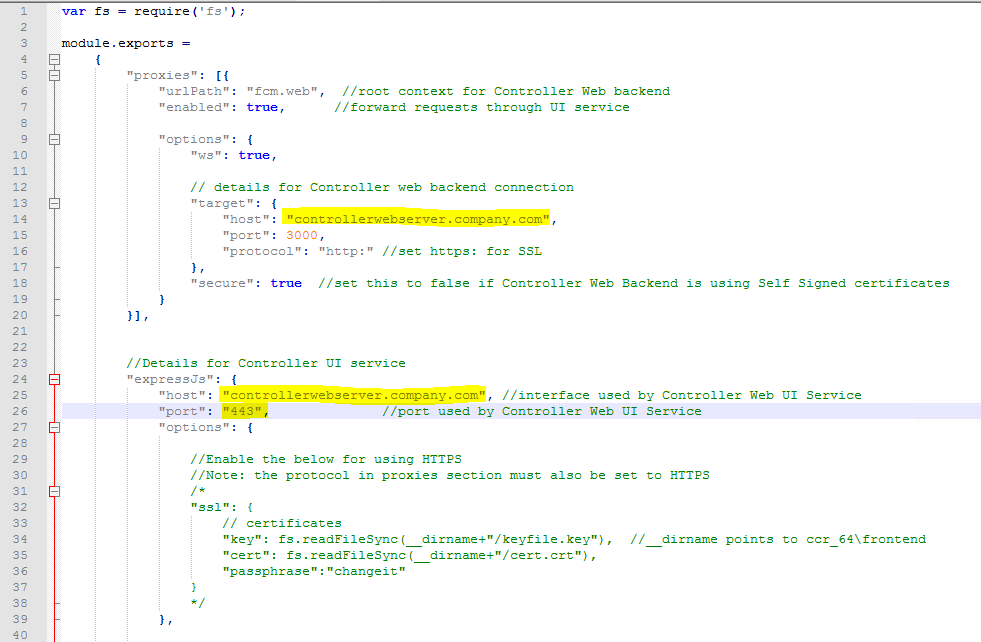
Change first host value to “host”: “controllerwebserver.company.com“,
Change second host value to “host”: “controllerwebserver.company.com“, //interface used by Controller Web UI Service
Change the port to 443 from 9080.
Save the file.
Restart the IBM Cognos Controller Web UI Windows Service.
Try to browse to http://controllerwebserver.company.com:443/ from client laptop.
Check that the windows firewall on the server allow ports 80,443,9300
If you are using SSO modify the IIS website’s controllerserver virtual directory to use anonymous authentication, only have Windows authentication on the sso virtual directory.
If you get a blank page in web browser when browse to Controller web, check
the Internet Explorer settings, to disable Compatability View mode.
Get the Certificates for you controllerwebserver.company.com servers DNS alias from the company Certificate Authority. You need the root cert (root1.cer) and the intermediate cert (intermediate2.cer), also the pfx file for the servername and chain (servername3.pfx) with a password.
During setup use the same password for all keys and keystores, in our example we will use changeit.
Start a CMD command prompt as Administrator
Go to folder c:\Program Files\ibm\cognos\ccr_64\fcmweb\jre\bin
Update this command with your certificate files, before you run it:
keytool -keystore key.jks -importcert -file C:\temp\intermediate2.cer
Enter the password (must be the same as the password you got with the pfx file)
On question ‘Trust this certificate’ enter yes
Import the root1.cer file with command:
keytool -import -trustcacerts -alias issue -file c:\temp\root1.cer -keystore key.jks
Add the server-certificate with command:
keytool -importkeystore -destkeystore key.jks -srckeystore C:\temp\servername3.pfx -srcstoretype PKCS12 -srcstorepass changeit
(replace the changeit with the password you got with the pfx file and you used before)
Copy the file key.jks to folder C:\Program Files\IBM\cognos\ccr_64\fcmweb\jre\lib\security
Open C:\Program Files\ibm\cognos\ccr_64\fcmweb\wlp\usr\servers\fcm.web\server.xml in Notepad++
Replace the line <!– <feature>ssl-1.0</feature> –> with <feature>ssl-1.0</feature>
Add a line at the bottom, like this:
</webApplication>
<keyStore id=”defaultKeyStore” password=”changeit” sslProtocol=”SSL_TLS” />
</server>
Save the file.
Restart the ‘IBM Cognos Controller Web UI’ and ‘IBM Cognos Controller Web’
Copy the file key.jks to folder C:\Program Files\IBM\cognos\ccr_64\fcmweb\wlp\usr\servers\fcm.web\resources\security
Open C:\Program Files\IBM\cognos\ccr_64\analytics\templates\ps\portal\variables_CCRWeb.xml in notepad++ and change to https;
<CRNenv c_cmd=”https://controllerwebserver.company.com:443/#!/CamLogin”>
<cookies>
<param name=”cam_passport”/>
</cookies>
</CRNenv>
Open C:\Program Files\IBM\cognos\ccr_64\fcmweb\wlp\usr\servers\fcm.web\com.ibm.cognos.fcm.web.properties in notepad++
Change line ccrwsUrl=https://cognosserver.company.com/ibmcognos/controllerserver/ccrws.asmx and biUrl=https://cognosserver.company.com/ibmcognos/bi/v1/disp to use https if you only have SSL on the IIS server for CA11.
Save the file.
Delete the key.p12 file from folder C:\Program Files\IBM\cognos\ccr_64\fcmweb\wlp\usr\servers\fcm.web\resources\security
Reboot the controllerweb windows server.
Check filer C:\Program files\ibm\cognos\ccr_64\fcmweb\wlp\usr\servers\fcm.web\logs\messages.log for , if no error go one with next step.
One your laptop install openssl from here https://github.com/git-for-windows/git/releases/tag/v2.23.0.windows.1 – get the file Git-2.23.0-64-bit.exe. Run the installation with all default values.
Copy your servername3.pfx file to c:\workarea folder. Start a CMD command prompt as Administrator.
Run this command:
“C:\Program Files\git\mingw64\bin\openssl.exe” pkcs12 -in C:\workarea\servername3.pfx -clcerts -nokeys -out cert.crt
Enter the password you got with the pfx file.
“C:\Program Files\git\mingw64\bin\openssl.exe” pkcs12 -in C:\workarea\servername3.pfx -nocerts -out keyfile.key
Enter the password you got with the pfx file. Then you have to give a new password for the keyfile.key – for simplicity use the same password.
Copy cert.crt , keyfile.key files to C:\Program Files\ibm\cognos\ccr_64\frontend folder on your Controller Web server.
Open C:\Program Files\IBM\cognos\ccr_64\frontend\config.js file in Notepad++
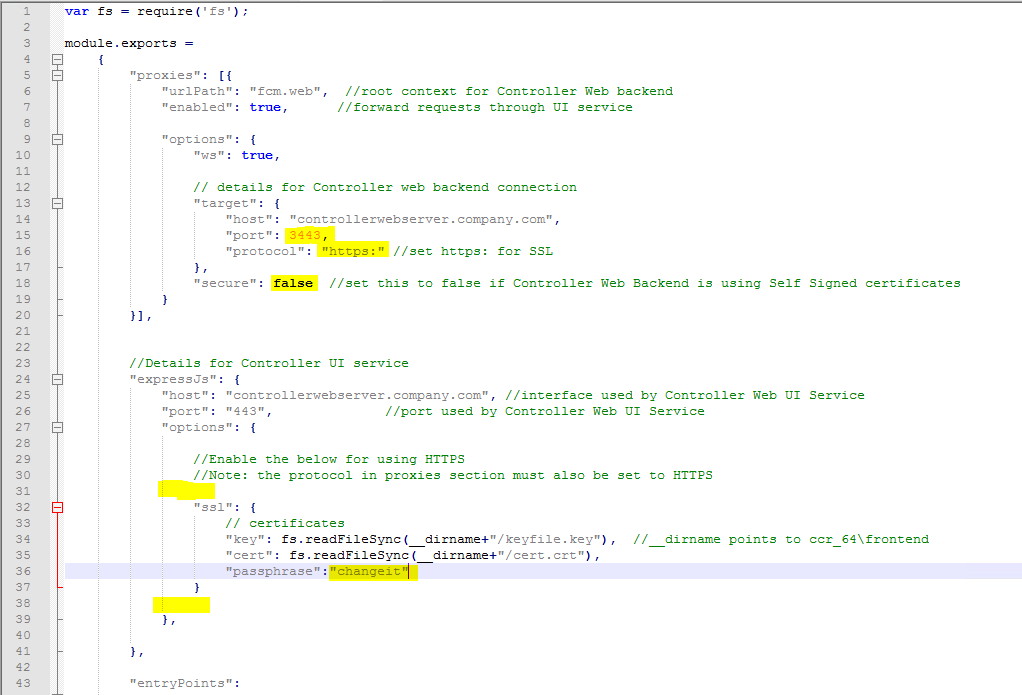
Change the first port to “port”: 3443,
Change the protocol to “protocol”: “https:” //set https: for SSL
Change secure to “secure”: false //set this to false if Controller Web Backend is using Self Signed certificates
Remove /* */ to uncomment the SSL section.
Change the “passphrase”:”changeit” to your password that you set before.
Save the file.
Restart the ‘IBM Cognos Controller Web UI’ and ‘IBM Cognos Controller Web’
Try to browse to https://controllerwebserver.company.com/ from client laptop.
Check the log files in folder C:\Program Files\ibm\cognos\ccr_64\fcmweb\wlp\usr\servers\fcm.web\logs
This page can’t be displayed. Turn on TLS 1.0, TLS 1.1, and TLS 1.2 in Advanced settings and try connecting to https://hostname again. If this error persists, it is possible that this site uses an unsupported protocol or cipher suite such as RC4 (link for the details), which is not considered secure. Please contact your site administrator.
If you get above error, please try first with different web browser, like Firefox or Edge.
Error:
00000022 com.ibm.ws.ssl.provider.AbstractJSSEProvider E CWPKI0813E: Error while trying to initialize the keymanager for the keystore [C:/Program Files/ibm/cognos/ccr_64/fcmweb/wlp/usr/servers/fcm.web/resources/security/key.jks]. The private key password is not correct or the keystore has multiple private keys with different passwords. This keystore can not be used for SSL. Exception message is: [Cannot recover key].
00000022 com.ibm.ws.logging.internal.impl.IncidentImpl I FFDC1015I: An FFDC Incident has been created: “java.security.UnrecoverableKeyException: Cannot recover key: invalid password for key in file ‘C:/Program Files/ibm/cognos/ccr_64/fcmweb/wlp/usr/servers/fcm.web/resources/security/key.jks’ com.ibm.ws.ssl.provider.IBMJSSEProvider getKeyTrustManagers” at
Solution:
The pfx file password was not used in creation of the key.jks file
Error:
00000022 com.ibm.ws.ssl.config.WSKeyStore E CWPKI0033E: The keystore located at C:/Program Files/ibm/cognos/ccr_64/fcmweb/wlp/usr/servers/fcm.web/resources/security/key.jks did not load because of the following error: Keystore was tampered with, or password was incorrect
00000022 com.ibm.ws.ssl.config.WSKeyStore W CWPKI0809W: There is a failure loading the defaultKeyStore keystore. If an SSL configuration references the defaultKeyStore keystore, then the SSL configuration will fail to initialize.
Solution:
The password in the server.xml file is not the same as the key.jks file.
Error:
00000022 com.ibm.ws.logging.internal.impl.IncidentImpl I FFDC1015I: An FFDC Incident has been created: “java.security.UnrecoverableKeyException: Cannot recover key: invalid password for key in file ‘C:/Program Files/ibm/cognos/ccr_64/fcmweb/wlp/usr/servers/fcm.web/resources/security/key.jks’ com.ibm.ws.ssl.provider.IBMJSSEProvider getKeyTrustManagers” at
Solution:
Maybe you use different password in servername3.pfx and key.jks file
Error:
00000022 com.ibm.ws.ssl.config.WSKeyStore E CWPKI0033E: The keystore located at C:/Program Files/ibm/cognos/ccr_64/fcmweb/wlp/usr/servers/fcm.web/resources/security/key.jks did not load because of the following error: Keystore was tampered with, or password was incorrect
00000022 com.ibm.ws.ssl.config.WSKeyStore W CWPKI0809W: There is a failure loading the defaultKeyStore keystore. If an SSL configuration references the defaultKeyStore keystore, then the SSL configuration will fail to initialize
Solution:
The key.jks file is not copied to C:\Program Files\IBM\cognos\ccr_64\fcmweb\wlp\usr\servers\fcm.web\resources\security after update.
If you get “Not authorized” when logon to Controller Web when SQL server is setup to only allow TLS 1.2 communication.
1. Go to the folder C:\Program Files\ibm\cognos\ccr_64\fcmweb\wlp\etc\
2. Open the jvm.options file in NOTEPAD++
3. Add the following lines (at the end):
-Dcom.ibm.jsse2.overrideDefaultTLS=true
-Dcom.ibm.jsse2.overrideDefaultProtocol=TLSv12
4. Save changes
Restart the Controller web service.
More Information:
https://www.ibm.com/support/pages/how-configure-controller-web-use-ssl-https
https://www.ibm.com/support/pages/node/563063
https://www.ibm.com/support/pages/node/156485
https://www.ibm.com/support/knowledgecenter/en/SSEP7J_11.0.0/com.ibm.swg.ba.cognos.inst_cr_winux.doc/t_configuresslforcognos8.html
https://www.ibm.com/support/pages/how-configure-force-controller-use-tls-12
https://www.ibm.com/support/pages/how-configure-controller-use-tls-formerly-ssl-connect-microsoft-sql-database-transit-database-encryption?lnk=hm
https://support.microsoft.com/en-us/help/17479/windows-internet-explorer-11-change-security-privacy-settings
https://www.ibm.com/support/pages/troubleshooting-controller-web-page-blankwhite
https://www.ibm.com/support/pages/not-authorized-when-logon-controller-web-caused-missing-tls-encryption-options-jvmoptions-configuration-file