Product:
Planning Analytics Workspace version 38
Planning Analytics 2.0.5
Linux Red Hat 7
Problem:
A security scan show that the PAW on port 443 try to use old ciphers sets.
The server is configured to support ciphers known as static key ciphers. These ciphers don’t support “Forward Secrecy”. In the new
specification for HTTP/2, these ciphers have been blacklisted.
Negotiated with the following insecure cipher suites:
TLS 1.1 ciphers:
TLS_RSA_WITH_AES_128_CBC_SHA
TLS_RSA_WITH_AES_256_CBC_SHA
TLS_RSA_WITH_CAMELLIA_128_CBC_SHA
TLS_RSA_WITH_CAMELLIA_256_CBC_SHA
TLS 1.2 ciphers:
TLS_RSA_WITH_AES_128_CBC_SHA
TLS_RSA_WITH_AES_128_CBC_SHA256
TLS_RSA_WITH_AES_128_GCM_SHA256
TLS_RSA_WITH_AES_256_CBC_SHA
TLS_RSA_WITH_AES_256_CBC_SHA256
TLS_RSA_WITH_AES_256_GCM_SHA384
TLS_RSA_WITH_CAMELLIA_128_CBC_SHA
TLS_RSA_WITH_CAMELLIA_256_CBC_SHA
Possible Solution:
Configure the server to disable support for static key cipher suites.
Login to the PAW Linux server with PUTTY.
Change to the user who have access to the paw folder (e.g. dockeruser).
Go to the /ibm/paw/config folder.
Check the content of defaults.env with the command more defaults.env to see the current used values.
Open paw.env file with command nano paw.env
Add below two rows;
export SSLCipherSuite=”ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSAAES256-
GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256″
export SSLProtocol=”all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1″
Save the file with ctrl+o
Exit nano program with ctrl+x
Restart the PAW server.
Check this link for what values to set in SSLCipherSuite:
https://mozilla.github.io/server-side-tls/ssl-config-generator/
If it does not work, revert back to the original settings shown below, by simple remove the two lines from the paw.env file.
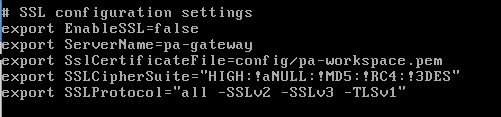
export SSLProtocol=”all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1″
above means all protocols except the one listed after the minus, so no SSLv2 or SSLv3 or TLSv1 or TLSv1.1, leaving only TLSv1.2 to show.
The way you created the certificate request when you setup SSL(TLS) for PAW, can affect the ciphers you can use.
More Information:
https://electricenergyonline.com/print_article.php?ID=779
http://www.nist.gov/manuscript-publication-search.cfm?pub_id=915295
https://wiki.mozilla.org/Security/Server_Side_TLS
http://support.microsoft.com/kb/245030/
https://tools.ietf.org/html/rfc7540/