Product:
Planning Analytics 2.0.5
Microsoft Windows 2016 server
Problem:
A security audit list that the access to TM1 Admin service is not enough secure. Port 5498 and 5898 show this;
Negotiated with the following insecure cipher suites:
TLS 1.0 ciphers:
TLS_RSA_WITH_3DES_EDE_CBC_SHA
TLS_RSA_WITH_AES_128_CBC_SHA
TLS_RSA_WITH_AES_256_CBC_SHA
TLS 1.1 ciphers:
TLS_RSA_WITH_3DES_EDE_CBC_SHA
TLS_RSA_WITH_AES_128_CBC_SHA
TLS_RSA_WITH_AES_256_CBC_SHA
Vulnerability Solution:
Enable support for at least one of the ciphers listed below:
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
TLS_DHE_DSS_WITH_AES_128_GCM_SHA256
TLS_DHE_DSS_WITH_AES_256_GCM_SHA384
TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
Possible solution:
Inside the Cognos Configuration the TM1 Admin server value for Support pre-TLS v1.2 clients are set to TRUE, this should be set to False to solve above issue.
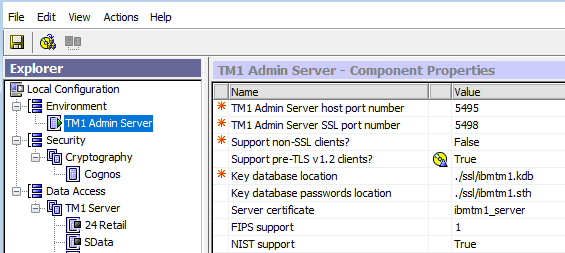
Change to FALSE,
Save settings.
At the restart of the TM1 Admin Server, all the TM1 running instances will be restarted, this can take time. Do this at a planned date.
More information about ports:
http://www.practicallynetworked.com/sharing/app_port_list.htm
http://www.networksorcery.com/enp/protocol/ip/ports04000.htm
Ports used by CA11
https://www.ibm.com/support/knowledgecenter/en/SSEP7J_11.0.0/com.ibm.swg.ba.cognos.inst_cr_winux.doc/c_reviewthedefaultsettings.html
Ports used by PAL
https://www.ibm.com/support/knowledgecenter/en/SSD29G_2.0.0/com.ibm.swg.ba.cognos.tm1_inst.2.0.0.doc/c_tm1_inst_defaultvaluesfortm1installation.html
This can also help secure the TM1 Admin service;
| TM1 Admin Server Certificate Version | Specifies which version of the TM1 generated certificates to use.
By default, the 1024-bit encryption version of the TM1 generated certificates is used. Change this property only if you want to use the new 2048-bit encryption version of the default certificates. You can use the new version with old and new TM1 clients, but you must configure the clients to use the new certificate authority file. Note This property does not apply if you are using your own certificates.
Valid values include:
|