Product:
Cognos Analytics
Microsoft Windows 2016 server
Issue:
How do i check my computer for this issue?
Suggested solution:
Paste below code in a text file, name the file to check.ps1
gci 'C:\' -rec -force -include *.jar -ea 0 | foreach {select-string "JndiLookup.class" $_} | select -exp Path
Place the file in c:\temp and start a powershell session:
.\check.ps1 > result.txt
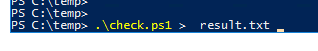
Run the file with pipe the result to a text file, so you later easy can check what files can be an issue.
The command will check in jar files if they have the string JndiLookup.class
It will list the jar files that can have the issue, one example is C:\Program Files\ibm\cognos\analytics\bin\ThirdPartyCertificateTool.jar. Think that this program is not running all the time, it is only used when you use the tool from the command line. Then this jar file have a very little risk. It is worse for web-servers and web applications that run all the time.
You can unzip a jar file, to check its content.
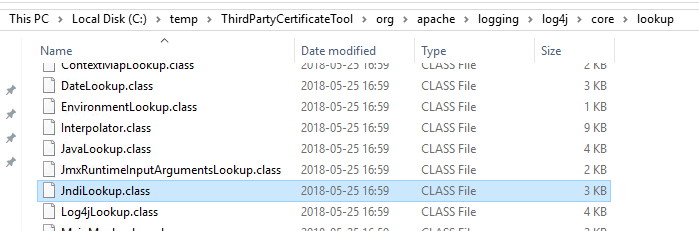
If you remove the file JndiLookup.class and zip it back to a JAR file, you have cleaned the program.
More information:
https://www.ibm.com/support/pages/node/6526474
https://www.ibm.com/blogs/psirt/an-update-on-the-apache-log4j-cve-2021-44228-vulnerability/
Within IBM Planning Analytics 2.0, only the IBM Planning Analytics Workspace component of IBM Planning Analytics is affected by a security vulnerability. Apache Log4j is used by IBM Planning Analytics Workspace as part of its logging infrastructure. This bulletin addresses the exposure to the Apache Log4j (CVE-2021-44228) vulnerability.
Log4j 1.2.17 and 1.x does not contain any of the same lookup / template evaluation code, and the only class related to JNDI (JMSAppender) does not appear to connect to user-controlled remote systems based on log events. Older version of Cognos Controller that uses log4j-1.2.7.jar, does not have the same issue.