Product:
Cognos Controller 10.4.2
Microsoft Windows 2019 server
Issue:
When setup HTTPS for Cognos Controller web, need to convert the jks file to keyfile.key and cert.cer
https://www.ibm.com/support/pages/how-install-controller-web
https://www.ibm.com/support/pages/how-configure-controller-web-use-ssl-https
Solution:
If you setup HTTPS/TLS/SSL for Cognos Analytics on the same server as you have Cognos Controller installed, then you may want to use that certificate for the Controller Web installation.
(This is a summary of some of the steps – you may need to do additional steps to get HTTPS to work for you).
CA11 is setup with commands like this:
ThirdPartyCertificateTool.bat -c -e -p NoPassWordSet -a RSA -r "request.csr" -d "CN=servername.domain.com,OU=department,O=company,L=place,C=SE" -H "servername.domain.com"
Above to create a certificate request, that you can send to your company CA. This will update the CAMKeystore file in the install_location\configuration\certs directory.
The pem file you get from the company CA, needs to be separated up into 4 files with a certificate in each. You can use Notepad++ for this.
Then import the pem files with below command.
ThirdPartyCertificateTool.bat -i -T -r root.pem -p NoPassWordSet ThirdPartyCertificateTool.bat -i -T -r issuing.pem -p NoPassWordSet ThirdPartyCertificateTool.bat -i -e -r server.pem -t chain.pem -p NoPassWordSet
Update Cognos Configuration to HTTPS/443 and under Certificate Authority settings, click the Use third party CA property, and set its Value to True.
Save and restart CA11 service.
Import the p7b cert into IIS, and configure its bindings to use HTTPS.
Update the IIS settings with the file CA_IIS_CONFIG.BAT.
Change Cognos Controller Configuration to support HTTPS.
https://www.ibm.com/support/pages/how-enable-ssl-https-cognos-controller
To get a key.jks file from the CAMkeystore, start IKEYMAN.EXE as administrator.
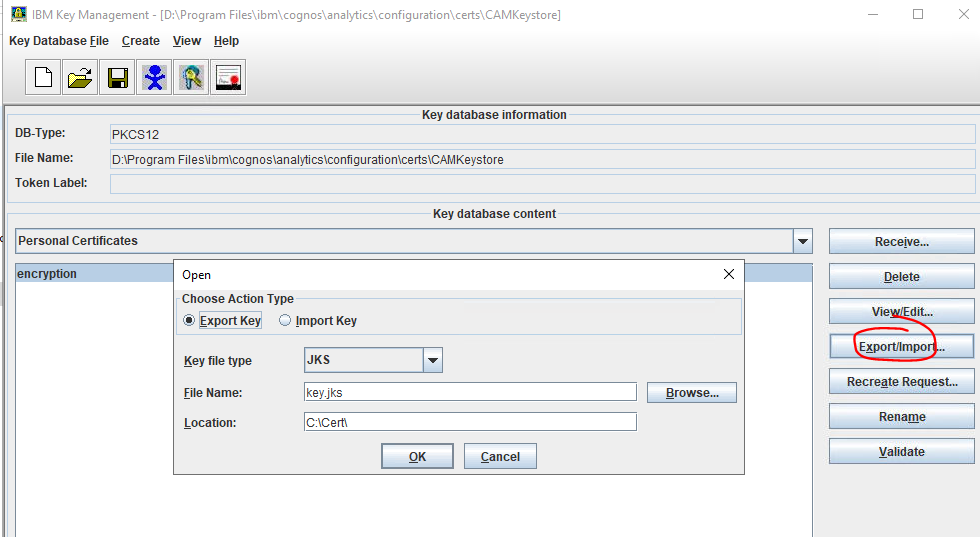
Open the D:\Program Files\ibm\cognos\analytics\configuration\certs\CAMkeystore file.
Select personal certificate: encryption and click on export button.
Select Export Key.
Select the folder where you want to store the key.jks file.
Press OK and set a new password: changeit
Then you have a key.jks file with the content of the CAMkeystore.
Put the *.pem files you created before in c:\cert\ folder and use below commands to import them in a key.jks file for controller web.
Start a DOS prompt and change to controller web folder:
cd d:\Program Files\ibm\cognos\ccr_64\fcmweb\jre\bin keytool -keystore key.jks -importcert -file C:\Cert\issuing.pem -alias issuing1 keytool -import -trustcacerts -alias root1 -file C:\Cert\root.pem -keystore key.jks keytool -importkeystore -destkeystore key.jks -srckeystore C:\Cert\key.jks -srcstorepass changeit
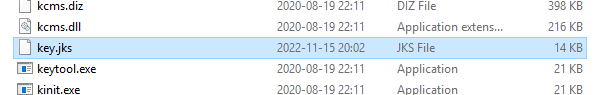
Restart the Controller Web service. Copy key.jks file in folder D:\Program Files\ibm\cognos\ccr_64\fcmweb\jre\bin to folder ..\lib\security.
Open d:\Program Files\ibm\cognos\ccr_64\fcmweb\wlp\usr\servers\fcm.web\server.xml in Notepad++
Remove brackets around “<feature>ssl-1.0</feature>”
Add below line last
</webApplication> <keyStore id="defaultKeyStore" password="changeit" sslProtocol="SSL_TLS" /> </server>
Save the file and restart the Controller Web services.
Copy the file …jre\bin\key.jks to D:\Program Files\ibm\cognos\ccr_64\fcmweb\wlp\usr\servers\fcm.web\resources\security folder.
Edit the file d:\Program Files\IBM\cognos\ccr_64\analytics\templates\ps\portal\variables_CCRWeb.xml to use correct port number 9081.
Edit the file com.ibm.cognos.fcm.web.properties in Notepad++ to have https instead of http.
Reboot the Cognos Controller Web server.
For the Cognos Controller Web frontend you need to extract the key and certificate from your jks file.
To extract the certificate for the server use this command:
keytool -export -alias encryption -file C:\Cert\cert.crt -keystore C:\Cert\key.jks
(The alias was encryption in the CAMkeystore file, therefor is it the same in the key.jks file)
To find if a certificate for a server exist in a jks file use this command:
keytool -list -v -srckeystore C:\Cert\key.jks | findstr "server001"
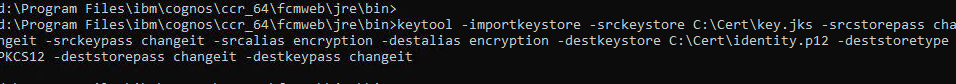
To extract the key from a jks file, you must first convert it to a pck12 file with this command:
keytool -importkeystore -srckeystore C:\Cert\key.jks -srcstorepass changeit -srckeypass changeit -srcalias encryption -destalias encryption -destkeystore C:\Cert\identity.p12 -deststoretype PKCS12 -deststorepass changeit -destkeypass changeit
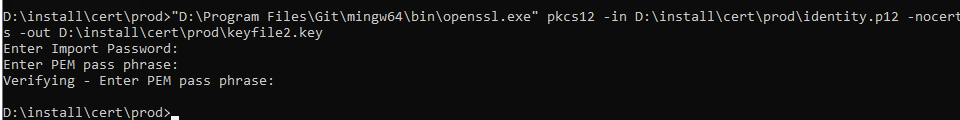
Now you have the file identity.p12 that you can copy to a server where you have openssl installed, so you can export the key with command:
"D:\Program Files\Git\mingw64\bin\openssl.exe" pkcs12 -in D:\install\cert\prod\identity.p12 -nocerts -out D:\install\cert\prod\keyfile2.key
Copy both of the above resulting files (cert.crt , keyfile2.key) to the following folder D:\Program Files\ibm\cognos\ccr_64\frontend.
Open config.js from folder D:\Program Files\ibm\cognos\ccr_64\frontend
Edit to
- Proxies – options – target – port : 3443
- Proxies – options – target – protocol : “https:”
- Proxies – options – secure : false
- expressJs – port : “9081”
- Enable the ssl section, by uncommenting out the relevant lines
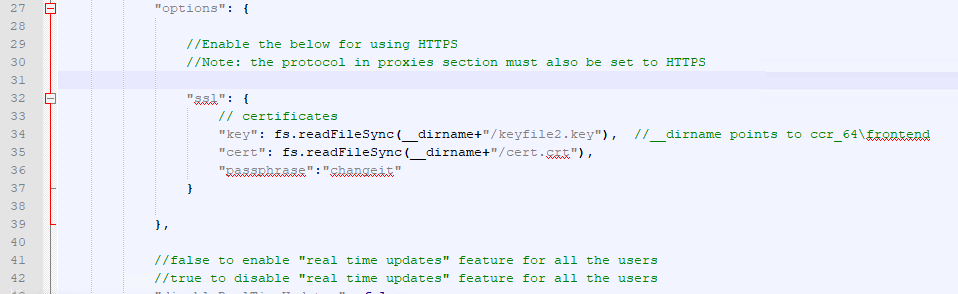
Save the file and and restart the Controller web service.
Check for errors in folder D:\Program Files\ibm\cognos\ccr_64\frontend\logs and D:\Program Files\ibm\cognos\ccr_64\fcmweb\wlp\usr\servers\fcm.web\logs
Error like: Error: error:0906D06C:PEM routines:PEM_read_bio:no start line
Then you have to do the steps again – as one of the files are wrong.
In case the above jks does not work – do it again but with a pfx-file.
You can export a p12 file from IKEYMAN, then only rename the p12 file to pfx. Then you have a pfx file.
cd d:\Program Files\ibm\cognos\ccr_64\fcmweb\jre\bin keytool -keystore key.jks -importcert -file C:\Cert\fromcamkey\issuecert.arm -alias issuing2 keytool -import -trustcacerts -alias root2 -file C:\Cert\fromcamkey\rootcert.arm -keystore key.jks keytool -importkeystore -destkeystore key.jks -srckeystore C:\Cert\fromcamkey\camkey.pfx -srcstoretype PKCS12 -srcstorepass changeit
Then copy the pfx to your computer where OPENSSL is installed, and do this commands to get out the files to frontend folder.
"D:\Program Files\Git\mingw64\bin\openssl.exe" pkcs12 -in D:\install\cert\prod\camkey.pfx -clcerts -nokeys -out D:\install\cert\prod\cert3.crt "D:\Program Files\Git\mingw64\bin\openssl.exe" pkcs12 -in D:\install\cert\prod\camkey.pfx -nocerts -out D:\install\cert\prod\keyfile3.key
Copy the cert3.crt and keyfile3.key to the folder D:\Program Files\ibm\cognos\ccr_64\frontend on controller web server.
Update the config.js file for above new file names.
Reboot the cognos controller web server.
More information:
https://security.stackexchange.com/questions/98282/difference-between-openssl-and-keytool
Keytool is a tool that comes with Java that works with KeyStores – it can create KeyStores and manipulate keys and certificates inside them. It can also create keys and sign certificates. So it is both a key generation and a KeyStore-file-administration tool.
OpenSSL works with standard formats (PEM/CER/CRT/PKCS/etc) but does not manipulate KeyStore files. It is possible to generate a key and/or certificate with OpenSSL, and then import that key/cert into a KeyStore using keytool, but you can’t put the key/cert into the KeyStore directly using OpenSSL.
Both OpenSSL and keytool have the same purpose: generating/storing keys and certificate(s) (chaines). The thing is that Java can only work with certificates/keys contained within its keystore (JKS). Those certificates and keys are generated using the keytool library, not by using openssl.
Java keytool will always need a keystore in order to store the certificates and keys it has generated, where this is not the case for openssl. Do note that OpenSSL can also be used to create a similar container, namely PKCS12 (.p12). This is a password protected container containing keys and certificates (just like Java’s keystore). However, it’s not compatible with Java… You’d need to convert the .p12 container to .jks before your Java application will be able to work on the certificates.
https://www.ibm.com/support/pages/how-export-private-key-and-public-key-keystore
https://dzone.com/articles/extracting-a-private-key-from-java-keystore-jks
https://www.sslshopper.com/article-most-common-java-keytool-keystore-commands.html
https://docs.oracle.com/javase/7/docs/technotes/tools/solaris/keytool.html