Product:
Cognos Analytics 11.1.7
Microsoft Windows 2019 server
Issue:
Should i do something for Cognos products because of the Log4j vulnerability?
There is now a “patch”….. read more here https://www.ibm.com/support/pages/node/6526474
Security Bulletin: IBM Cognos Analytics: Apache log4j Vulnerability (CVE-2021-44228)
https://www.ibm.com/support/pages/node/6538720
Background:
https://thehackernews.com/2021/12/apache-log4j-vulnerability-log4shell.html
By sending a specially crafted code string, an attacker could exploit this vulnerability to load arbitrary Java code on the server and take complete control of the system. The attacker must get the Cognos Logger software to process a string to the log file, that active the function JNDI to contact LDAP server xxxx and download information, that in real can be java code, and execute it. Gives the possibility to install Trojans and other software, but he need to trick cognos to send the information to the logger.
Suggested Solution:
First check what IBM say, if needed for cognos, they will release patch or instructions on there page.
https://www.ibm.com/blogs/psirt/an-update-on-the-apache-log4j-cve-2021-44228-vulnerability/
Things you can do:
Ensure that the Cognos servers do not have contact with Internet, so any application on the server can reach out and download other software.
Creating a default-deny firewall rule will prevent servers from creating unapproved connections and can help reduce your risk of a compromise.
Ensure that only the people and computers that need it, have access to your cognos servers.
You can use tools, to see if you have the vulnerability;
https://log4shell.huntress.com/
https://github.com/xforcered/scan4log4shell
Log4j is a tool to create log files, used by WebSphere and maybe Cognos software.
Check version of WebSphere with this command:
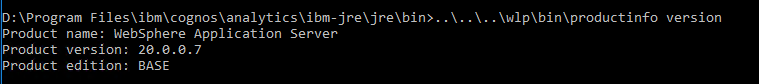
Above is from CA11.1.x CM_version=11.1.7-41.
In a CMD prompt, go to the java bin folder (path depends on version of Cognos Analytics)
Enter command C:\Program Files\ibm\cognos\analytics\wlp\bin\productinfo version
CA11 uses WebSphere Liberty Server, where the version number is the year it was released.
WebSphere Application Server (WAS) latest version is 9, that should correspond to WLP 20.
https://en.wikipedia.org/wiki/IBM_WebSphere_Application_Server
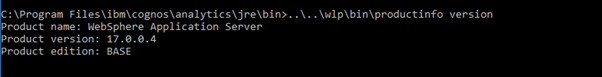
Above is from CA11.0.x CM_version=11.0.12.18
You can search your cognos folder, to see if you have Log4j files that can contain this issue.
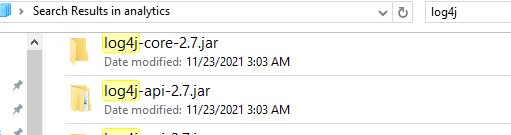
You will find it in several folders, but it is only the top one \bin that is the default. The others are cached versions in folders like C:\Program Files\ibm\cognos\analytics\wlp\usr\servers\cognosserver\workarea\org.eclipse.osgi\61\data\cache\com.ibm.ws.app.manager_157\.cache\WEB-INF\lib
Log4j-core and Log4j-api can contain this issue. Above picture from CA11, we see that we use version 2.7 of Log4j program. That is old, so the LOG4J_FORMAT_MSG_NO_LOOKUPS parameter will not work.
Versions of Log4j is listed here:
https://logging.apache.org/log4j/2.x/changes-report.html
If you can not wait for IBM instructions for Cognos, https://www.ibm.com/support/pages/node/6526474, you can test this in your LAB.
“the mitigation is to remove the JndiLookup class from the classpath, with command: zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class. ”
Stop the IBM Cognos service.
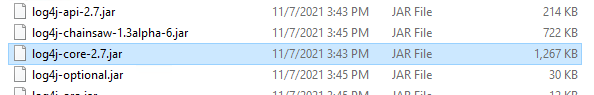
Copy the log4j-core-2.7.jar file to a new folder e.g. c:\tempfix
Unzip the jar file.
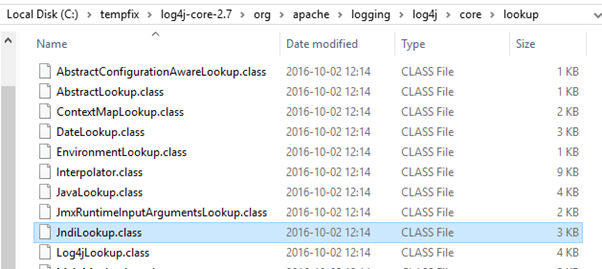
Go down in the unzipped folder structure to C:\tempfix\log4j-core-2.7\org\apache\logging\log4j\core\lookup folder
Remove the file JndiLookup.class
Go back to your top folder, and zip it again.
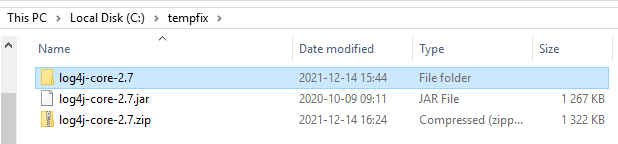
Rename your log4j-core-2.7.jar to log4j-core-2.7.org.jar ( to keep a backup ).
Rename your log4j-core-2.7.zip file to log4j-core-2.7.jar.
Copy the new log4j-core-2.7.jar file to your C:\Program Files\ibm\cognos\analytics\bin folder.
Start IBM Cognos.
Check that you can login and run reports.
The Log4j is used to create the cognosserver.log files, so carefully check that the log files work as expected.
https://docs.oracle.com/javase/tutorial/deployment/jar/build.html
https://www.freefileconvert.com/zip-jar
If your test work out well, you can update the C:\Program Files\ibm\cognos\analytics\bin\log4j-core-2.7.jar file on your other CA11 servers.
PAW have a fix at:
https://www.ibm.com/support/pages/node/6525316
https://www.ibm.com/support/pages/node/6192099
For the latest Cognos Controller version there is a new version out… but it may come more information from IBM.
TM1 may also not use the affected version. You have to check with IBM Support, what they say.
IBM SPSS have a fix at https://www.ibm.com/support/pages/node/6526182
IBM ILMT have a different version of Log4j, and therefor a different workaround:
Most product will have a “patch” to upgrade to later Log4j versions.
https://www.ibm.com/support/pages/node/6525762
Workaround 1. Manually upgrade Log4j library included in VM Manager Tool in versions 9.2.21.0 – 9.2.25.0 to version 2.15.0
- Download the Log4j library package in version 2.15.0 from this page: https://logging.apache.org/log4j/2.x/download.html and extract them.
- Copy the following files to the <VM_Manager_Tool_home_dir>/lib/ directory.
- log4j-api-2.15.0.jar
- log4j-core-2.15.0.jar
- Stop the VM Manager Tool by using the -stop switch of the <VM_Manager_Tool_home_dir>/vmman.sh|bat script. For more information, see: VM Manager Tool command-line options.
- Remove the following JAR files from the <VM_Manager_Tool_home_dir>/lib/ directory.
- log4j-api-2.13.3.jar
- log4j-core-2.13.3.jar
- Depending on your operating system, modify one of the following files.
- LINUX: In the <VM_Manager_Tool_home_dir>/vmman.sh file, find the following lines:
VMM_CLASS_PATH=$VMM_CLASS_PATH:$VMM_LOCAL_LIB/log4j-api-2.13.3.jar
VMM_CLASS_PATH=$VMM_CLASS_PATH:$VMM_LOCAL_LIB/log4j-core-2.13.3.jarChange them to:
VMM_CLASS_PATH=$VMM_CLASS_PATH:$VMM_LOCAL_LIB/log4j-api-2.15.0.jar
VMM_CLASS_PATH=$VMM_CLASS_PATH:$VMM_LOCAL_LIB/log4j-core-2.15.0.jar - WINDOWS: In the <VM_Manager_Tool_home_dir>/vmman.bat file, find the following lines:
SET VMM_CLASS_PATH=%VMM_CLASS_PATH%;%VMM_LOCAL_LIB%/log4j-api-2.13.3.jar
SET VMM_CLASS_PATH=%VMM_CLASS_PATH%;%VMM_LOCAL_LIB%/log4j-core-2.13.3.jarChange them to:
SET VMM_CLASS_PATH=%VMM_CLASS_PATH%;%VMM_LOCAL_LIB%/log4j-api-2.15.0.jar
SET VMM_CLASS_PATH=%VMM_CLASS_PATH%;%VMM_LOCAL_LIB%/log4j-core-2.15.0.jar
- LINUX: In the <VM_Manager_Tool_home_dir>/vmman.sh file, find the following lines:
- Start the VM Manager Tool by using -run switch of the <VM_Manager_Tool_home_dir>/vmman.sh|bat script. For more information, see: VM Manager Tool command-line options.
Workaround 2. Mitigate the issue on the current version of the Log4j library included in VM Manager Tool in versions 9.2.21.0 – 9.2.25.0 by the configuration change
- Depending on your operating system, run one of the following:
- LINUX: In the <VM_Manager_Tool_home_dir>/vmman.sh file, find the following line. It might not contain all the parameters starting with -D string, for example, it might not contain the -Dsun.net.http.allowRestrictedHeaders=true substring.VMM_PROPERTIES_DEFS=”-Dhttps.protocols=TLSv1.2,TLSv1.1,TLSv1 -Dcom.ibm.jsse2.disableSSLv3=false -Dcom.ibm.tools.attach.enable=no -Dsun.net.http.allowRestrictedHeaders=true”Add the following text at the end of the found line, just before the double quotation mark that ends this line.“ -Dlog4j2.formatMsgNoLookups=true” (including the space character at the beginning of the text)For example:
VMM_PROPERTIES_DEFS=”-Dhttps.protocols=TLSv1.2,TLSv1.1,TLSv1 -Dcom.ibm.jsse2.disableSSLv3=false -Dcom.ibm.tools.attach.enable=no -Dsun.net.http.allowRestrictedHeaders=true -Dlog4j2.formatMsgNoLookups=true“ - WINDOWS: In the <VM_Manager_Tool_home_dir>/vmman.bat file, add the following entry as the last line of the ####### PROPERTIES DEFINITONS ####### section:SET VMM_PROPERTIES_DEFS=%VMM_PROPERTIES_DEFS% -Dlog4j2.formatMsgNoLookups=true
- LINUX: In the <VM_Manager_Tool_home_dir>/vmman.sh file, find the following line. It might not contain all the parameters starting with -D string, for example, it might not contain the -Dsun.net.http.allowRestrictedHeaders=true substring.VMM_PROPERTIES_DEFS=”-Dhttps.protocols=TLSv1.2,TLSv1.1,TLSv1 -Dcom.ibm.jsse2.disableSSLv3=false -Dcom.ibm.tools.attach.enable=no -Dsun.net.http.allowRestrictedHeaders=true”Add the following text at the end of the found line, just before the double quotation mark that ends this line.“ -Dlog4j2.formatMsgNoLookups=true” (including the space character at the beginning of the text)For example:
- Stop the VM Manager Tool by using the -stop switch of the <VM_Manager_Tool_home_dir>/vmman.sh|bat script. For more information, see: VM Manager Tool command-line options.
- Start the VM Manager Tool by using the -run switch of the <VM_Manager_Tool_home_dir>/vmman.sh|bat script. For more information, see: VM Manager Tool command-line options.
Fixes:
https://gist.github.com/SwitHak/b66db3a06c2955a9cb71a8718970c592
https://www.ibm.com/blogs/psirt/an-update-on-the-apache-log4j-cve-2021-44228-vulnerability/
https://www.ibm.com/support/pages/node/6525762
https://www.ibm.com/support/pages/node/6526182
https://www.ibm.com/support/pages/node/6525706
More Information:
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44228
https://www.ibm.com/support/pages/17004-websphere-application-server-liberty-17004
https://www.ibm.com/support/pages/20002-websphere-application-server-liberty-20002
https://en.wikipedia.org/wiki/IBM_WebSphere_Application_Server#WebSphere_Liberty_Versions
https://securityintelligence.com/posts/apache-log4j-zero-day-vulnerability-update/
https://blog.cloudflare.com/inside-the-log4j2-vulnerability-cve-2021-44228/
https://nvd.nist.gov/vuln/detail/CVE-2021-44228
https://www.skylit.com/javamethods/faqs/createjar.html
https://success.trendmicro.com/solution/000289940
https://bishopfox.com/blog/log4j-zero-day-cve-2021-44228
You have to decide how you will handle this possible threat in your organization.
This is only a list of information, on the subject.
You should check your logs from your antivirus / firewall software, if you are already compromise.
The IBM Cognos Analytics team have developed a “no-upgrade” option for our “On Prem” (local installation) customers.
To get the patch, click this link: CA-11.x-Log4jSafeAgent
For detailed instructions, see Mitigate the Apache Log4j vulnerability (CVE-2021-44228) in Cognos Analytics
| Affected Version | Fix Version | Bundled Customers |
| IBM Cognos Analytics 11.2.x | Cognos Analytics 11.2.1 Interim Fix 1
|
IBM Cognos Analytics 11.2.1 Interim Fix 2 (Bundled) |
| IBM Cognos Analytics 11.1.x
|
Cognos Analytics 11.1.7 Interim Fix 6
|
IBM Cognos Analytics 11.1.7 Interim Fix 7 (Bundled) |
| IBM Cognos Analytics 11.0.6 to 11.0.13 FP4
|
Cognos Analytics 11.0.13 Interim Fix 3
|
IBM Cognos Analytics 11.0.13 Interim Fix 4 (Bundled) |
New version from 13 Jan 2022:
| Affected Version | Fix Version | Bundled Customers |
| IBM Cognos Analytics 11.2.x | IBM Cognos Analytics 11.2.1 Interim Fix 3
|
IBM Cognos Analytics 11.2.1 Interim Fix 3 (Bundled) |
| IBM Cognos Analytics 11.1.x
|
IBM Cognos Analytics 11.1.7 Interim Fix 8 | IBM Cognos Analytics 11.1.7 Interim Fix 8 (Bundled) |
| IBM Cognos Analytics 11.0.6 to 11.0.13 FP4
|
IBM Cognos Analytics 11.0.13 Interim Fix 5
|
IBM Cognos Analytics 11.0.13 Interim Fix 5 (Bundled) |